4 Data Security Risks For Your Business And How to Avoid the Trap
Data is the most precious asset for any business. Whether it’s financial reports, medical information, or a start-up company plan, it’s crucial to protect your data regardless of the sector you work in. Recently, data breach threats have been increasing despite tighter data protection regulations, putting businesses and their partners at financial risk. In fact, a data breach report from IBM and Ponemon Institute shows that data breach costs in 2021 were US$ 4.24 Million. This is 10 percent more than the average cost for 2019 at $3.86 million. Maintaining the security of your organization’s data against data security risks should be at the top of your list of crucial tasks, regardless of any legal or regulatory constraints.
Table of Contents
To keep your company from facing the same threats, it’s critical to understand the most prevalent forms of data breaches. Here are 4 data security risks for your business and what you can do to limit the risks they pose.
4 Most Common Data Security Risks in Most Businesses
Regardless of how small your organization may be, it is likely to be of interest to cybercriminals. Your digital assets, intellectual property, and the company will be better protected if you are informed of and have a basic grasp of the threats on the internet.
Though small and midsize businesses contain small-scale databases and significantly lesser information, any data kept on your computers is still vulnerable without proper data fortifications. Here are the four most common risks to data security that you need to be aware of right now.
Ransomware Attacks
Data in businesses of all sizes are in danger due to ransomware. Popular ransomware across the world is malware. It targets business computers and encrypts data, rendering it worthless without the decryption key. Attackers typically post a message known as a ransom note demanding money in exchange for releasing the key. However, in many situations, even doing so is useless, and the data loss happens.
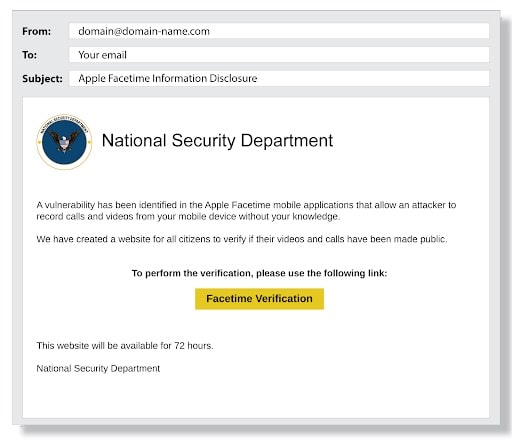
Phishing
One of the largest and most well-known cyber dangers to organizations is phishing. Verizon Data Breach Report (DBIR) 2021 states that phishing was used in 36 percent of breaches. It includes sending communications that look like they come from a reliable source but are sent by an attacker.
In one case, hackers sent an email with malware attached while acting as corporate leaders, gaining access to the private information of more than 20,000 federal agency workers.
Unintentional Leakage
A significant portion of data breaches happen due to careless or unintentional release of sensitive data rather than a deliberate attack. Employees frequently share, allow access to, mishandle, lose, or disclose valuable data accidentally or because they are unaware of security procedures.
Unintentional data leaks, unfortunately, result in the same sanctions and reputational harm as intended ones. Data exposures from unintentional disclosure of sensitive information due to inadequate information security had impacted over 155.8 million people in 2020.

Malicious Insider Threat as Data Security Risk
A security risk known as an insider threat comes from within the targeted company. It usually involves a current or former employee or business acquaintance who gains unauthorized access to private data or privileged accounts on an organization’s network.
Malicious insiders and moles may also be responsible for more incidents that were not expected. Between March and July 2020, 27 percent of firms faced insider threats-related security breaches than in the five months prior to the pandemic, indicating an increase in cybersecurity issues due to the implications of unforeseen crisis.
Improve Your Data Security Posture and Protect Your Business
Numerous techniques and technologies exist to increase data security and digital safety. While no approach can thoroughly tackle the issue, companies may enormously enhance their security posture by combining many of the ones listed below.
Implement Access Controls to Minimize Data Security Risks
Since business owners manage who has access to and utilizes corporate data and resources, access controls are an essential component of data security. Through authentication and authorization, access control rules ensure that users have the proper access to business data and are who they claim to be.
Proper access control is used to:
- Lessen the risk of unauthorized access to physical and logical systems that might compromise security.
- Ensure that security technology and access control guidelines are in place to safeguard sensitive information
- Control who or what may see or use a specific resource regarding organization’s data
Continuously Upgrade Your Software
Professionals advise routinely updating all operating systems and application software. When patches are available, install them. When applications aren’t constantly patched and updated, your network is exposed. Microsoft’s Baseline Security Analyzer can be used to check that all programs are patched and current periodically. This is a simple and affordable solution to fortify your network and thwart potential assaults.
Data Masking
Data masking allows you to create a false version of data of organization that you can use for software testing and training purposes. It aims to provide a functional alternative to data when necessary.
There are many ways to modify data, such as encryption, character shuffling, and character or phrase substitution. No matter which method you use, the data must be changed in a way that is not reverse-engineered. Data masking preserves the data type but alters the values.
Data Encryption to Reduce Data Security Risks
This is a way to prevent hackers from accessing sensitive information. It is a requirement for many security strategies, and compliance standards require it.
Data encryption enables data to be converted from plaintext (readable text) to unreadable encoded (ciphertext). The data cannot be read or processed until the encryption key has been used. Public-key cryptography does not require sharing the decryption keys. Instead, the sender and the recipient have their keys used to perform encryption operations. This is, by design, more secure.
Another effective way to increase your digital safety is by applying NIS2 and zero-trust strategies. The updated NIS Directive now demands these strategies and can significantly enhance your organization’s security level.
Protecting the Integrity of Your Business’ Data Takes Effort
It may seem challenging to maintain the integrity of your vital company data by relying on traditional approaches. These are two-factor authentication dependence and in-house servers. Modern data integration solutions, however, offer a practical substitute by providing real-time fault identification and troubleshooting. If you are a first-time business owner, the decisions you make in the early years of your organization may be the most challenging and crucial. But it is the most important. It’s time to protect the integrity of your business’ data by watching out for common data security threats and finding a solution for them.

Magdalena Polka is a Business Solution Designer and an Information Technology / Project Management consultant and author with over 15 years of software development, management and project management experience.