Cybersecurity and Artificial Intelligence Relation: Improvement or Deficit?
In this “internet world” in which we live, cybersecurity and artificial intelligence have emerged as significant concerns. Recent years have seen an increase in the number of cyberattacks, record thefts, and identity fraud attacking sensitive systems, which pose a growing threat to society and individuals while changing the cybersecurity definition for everyone. And the development of artificial intelligence aided tools certainly have a part in it. Having contact with someone suffering from cold increases the likelihood of you contracting the illness yourself. Similar to this, organizations that add more connections to their systems enhance the chances for hackers to infiltrate their systems and inject viruses into the network.
Table of Contents
Millions of people, as well as a slew of organizations, have begun to feel the effects of such transgressions. In the UK, Cybersecurity breaches or assaults have been reported by four out of 10 corporations (39 %) and a quarter of charities (26%), according to a recent survey. Similarly to prior years, medium-sized enterprises (65 %), large corporations (64%), and high-income nonprofits are more likely to be in this category (51%)
What is artificial intelligence?
Artificial intelligence definition can be the computer science field that allows machines to appear as though they had human intellect in order to make them appear as natural as possible. With that in mind, artificial intelligence is a broad phrase used to refer to the progress of computer technology that does not rely on any living thing for its existence. Yet, it is generated entirely by artificial means and can exhibit similar actions and behaviors to humans.
Successful use of artificial intelligence has been demonstrated in nearly every scientific and industrial field to date. It is feasible to follow significant developments in every area where artificial intelligence is being applied, from healthcare systems to robots, and to do so in real-time. In this respect, it is one of the areas of the cyber world, cybersecurity, where artificial intelligence technologies are utilized the most extensively.
So, how exactly do the artificial intelligence and the cybersecurity definition correlate and counterattack?
What is cybersecurity definition?
Cybersecurity is the process of safeguarding computer systems, networks, and programs against digital intrusions and assaults. These cyberattacks are often intended to gain access to, alter, or delete sensitive information, extorting money from users, or interfere with routine company procedures and operations.
Cybersecurity has risen to the priority list because of the exponential expansion of data (both consumer and commercial). As a result, data breaches have become increasingly prevalent. The following are some of the most pervasive reasons for data breaches:
- Security credentials, such as passwords that are insecure or stolen
- Viruses, ransomware, and phishing schemes are all examples of malware.
- Insider risks using social engineering
- Inadequate IT system configuration, as well as user error
- Susceptible apps and improper permission administration create back doors.
The Other Side of The Coin: AI-enhanced Cyberattacks
The rising frequency of cyberattacks has prompted the introduction of artificial intelligence (AI) in cybersecurity definition to improve the efficiency and accuracy of data defenses. As was to be expected, artificial intelligence has also provided new powers to criminals.
Artificial intelligence makes it easier to develop intelligent defenses and threats. The most significant drawback of artificial intelligence is that it is equally available to everyone, including hackers. Hackers are employing artificial intelligence to launch multi-dimensional attacks in large numbers.
They are utilizing artificial intelligence to modify the malware and use technology to identify the most susceptible groups of individuals to exploit.
Prior to the advent of malware, hackers were highly competent programmers who could code their viruses and traverse complex security mechanisms. That is no longer the case; malware may now be marketed as an intelligent solution that can be installed or downloaded with a single click. As a result, non-computer skilled hackers are drawn into the battle, increasing the total number of hackers in the process.
In order to defend against such cybersecurity fails, an intelligent solution is required. By studying user activities, recognizing trends, and finding abnormalities in the network, a network monitoring tool based on artificial intelligence may rapidly uncover security risks and respond appropriately. It can identify, monitor, and close more cyberattack patterns than any human being is capable of.
What are Personal Cybersecurity Precautions, and why should you take them?
Self-initiated cybersecurity measures do not require that much technical expertise. Yet, they are primarily about managing our urges to procrastinate when creating & storing passwords, how we use, update, and secure our personal smart devices, and to what extent we are aware of our actions when surfing over the Internet. Let’s start with some chewable tips and tricks on personal cybersecurity to stick them in our minds.
- When doing shopping / or any information or commercial exchange with a website, it is necessary to look for the “HTTPS” term in the address line of the websites to ensure that they are secured.
- Furthermore, we should be mindful of the fact that public networks, which we see a lot of in public transportation and cafés, shouldn’t be utilized frequently or at all.
- If we are working in a public location, we must take precautions by using security apps like antivirus programs and VPNs. A virtual private network (VPN) encrypts and creates a secure network for your connection. While it is possible to use a free VPN service, utilizing a premium VPN service for commercial purposes may be more legitimate.
- We should constantly use the most recent version of the modems that we have at home or the office. Also, this principle applies to all Microsoft and iOS software updates on PCs and phones.
- If feasible, we should utilize third-party firmware recommended by the modem’s manufacturer to protect against sniffer attempts, and we should make sure that it is constantly up to date.
- Modems should not be used in their manufacturer default passwords.
- No matter what information is stored in our accounts, we should avoid using simple passwords. We should be cautious about upgrading our passwords between the periods of three and six months.
- We should avoid using the same password on several websites.
- We must back up our data regularly and keep our backups secure by using different passwords for each backup.
- We should not immediately click on any link without first reading it and giving it due consideration.
- We must be on the lookout for phishing attempts at all times (one of the common cybersecurity problems).
- We should be on the lookout for email sources that generate threats, and we should consult with others or IT personnel as necessary.
Final Thoughts
There is no conflict over that artificial intelligence offers many advantages in terms of security and usefulness over traditional methods. It makes our lives and finding information easier, the shopping experience more relevant, and it upgrades methods for tech professionals.
For example, some experts believe that artificial intelligence will soon enable us to live in a future where passwords are no longer required. New developments in the field of identification and access management demonstrate that a more sophisticated artificial intelligence-based device may be able to replace passwords in some situations.
While the same AI-based approaches may be used to take advantage of this potential, it is an issue of conscience and who chooses to use this power to change the artificial intelligence and cybersecurity definition at use. It is, hence, preferable to be safe than sorry!
Related Infographic
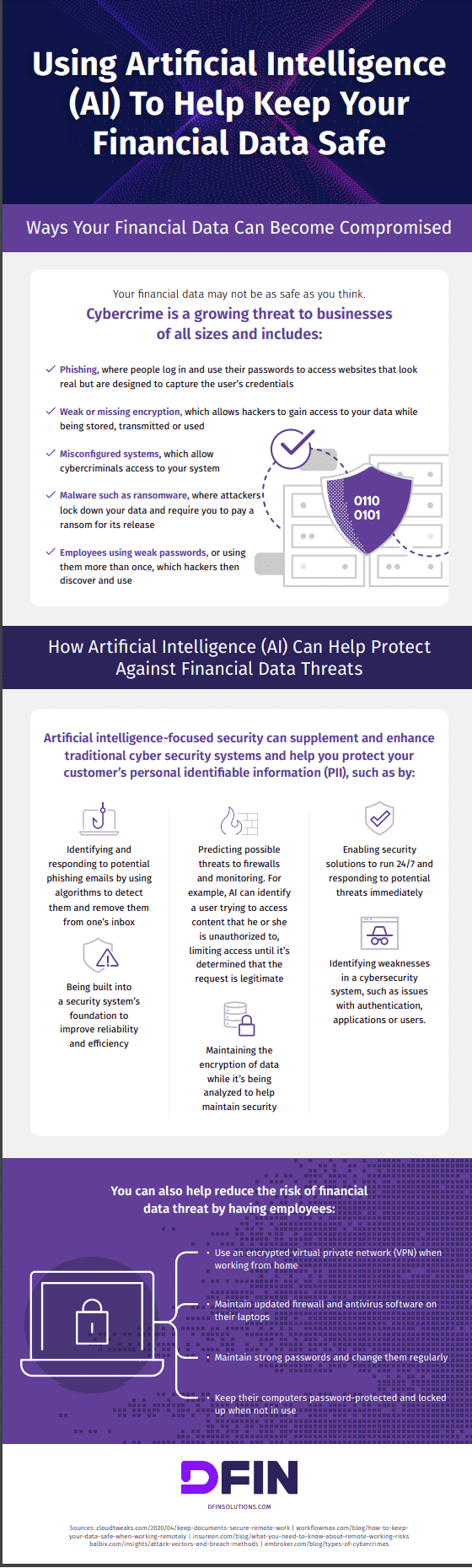
Infographic created by DFIN
Writing, researching, and learning about project management and tech.