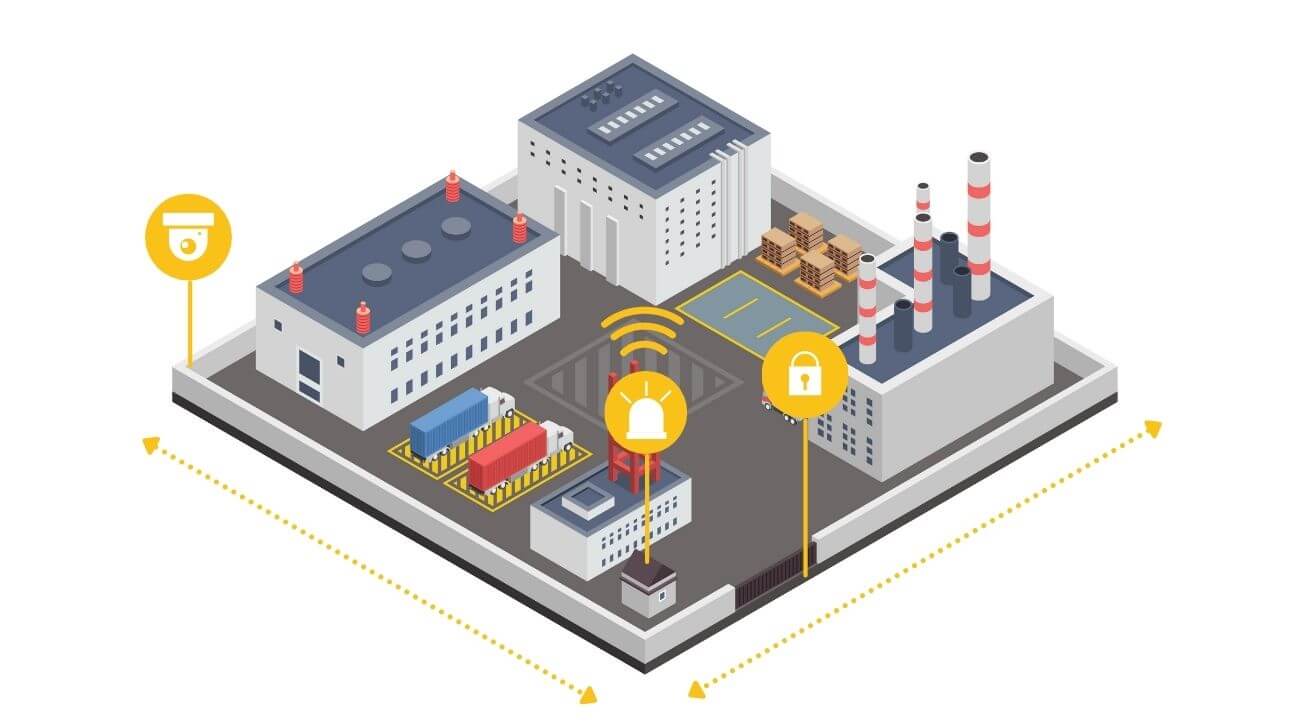
A Guide To Physical Security Infrastructure For Data Centers
Access control prevents unauthorized users from entering your data center as a part of Physical Security Infrastructure. Many modern businesses are investing in cloud-based access control due to the numerous benefits it provides for your security strategy, such as:
Table of Contents
- Remote management. You can easily view access logs and manage door lock status from anywhere using a mobile application or browser-based control center. These remote management features reduce time wasted traveling to the building’s entrance to unlock doors.
- Mobile credentials. A cloud-based access control system allows you to replace keycards and fobs with mobile credentials. This credential type is like a digital keycard that users can download to their mobile devices, making onboarding easier and reducing losses caused by keycard and fob replacement.
- Contactless entry. Users can quickly enter the building without pushing a button or swiping a keycard. They only need to wave their hand over the access control reader, triggering remote communication with their mobile device to unlock the door.
- First-time entry. The access control reader uses three modes of communication (WiFi, BlueTooth, and cellular) to ensure entry on the first attempt and allow traffic to flow smoothly into your building.
In addition to these advantageous features for Physical Security Infrastructure, cloud-based access control offers open API integrations, allowing you to expand your security hardware’s function with software integrations. Below are some of the best software integrations for protecting your data centers.
What is data center physical security?
Data center physical security refers to the measures and practices implemented to protect the physical infrastructure of a data center. This includes securing the building, controlling access to authorized personnel, monitoring and detecting unauthorized activities, and implementing safeguards to protect sensitive equipment and data housed within the data center facility.
What are the 3 main components of a data center infrastructure?
The three main components of a data center infrastructure are:
- Computing resources: This includes servers, storage devices, and networking equipment.
- Power and cooling systems: These systems provide electricity, backup power, and temperature control to ensure the proper functioning and protection of the equipment.
- Physical security measures: This includes access control, surveillance systems, and other measures to protect the data center from unauthorized access and physical threats.
Visitor Management Software
Keeping accurate visitor records improves your security strategy in the following ways:
- It allows you to have an accurate headcount for emergency evacuations.
- It provides records of who has accessed your building for security investigations.
Visitor management software automates the visitor management process, ensuring your data is reliable. Manual processes can be unreliable and lead to errors. The visitor management software application provides users digital registration forms to fill out on their mobile devices before entering the building.
You can log their details accurately for Physical Security Infrastructure. Once they have filled out the form, they can enter the building using temporary access credentials, which will be revoked when they leave. The system automatically logs their entry and exit times for airtight security processes.
Video Security And Access Control Integration
One of the most significant risks with any access control system is the potential for an unauthorized user to enter the building using stolen access credentials. So, you can integrate access control and video security for identity verification by leveraging open API integrations. By integrating both security tools, you can make both data sets accessible on a single interface.
If you suspect someone has used stolen access credentials to enter your building, you can verify this without correlating timestamps from different data sources for Physical Security Infrastructure. You can even integrate facial recognition software to automate identity verification and implement MFA at your building’s entrance.
Video Surveillance
Companies are now preferring smart building systems that are cloud-based over on-premise alternatives. This is because cloud-based video surveillance offers remote accessibility for security data. Your security staff can stay up-to-date with security threats and investigate potential breaches from anywhere using their mobile devices. Hence, this saves valuable time that would otherwise be wasted traveling to a control room.
Deploy a comprehensive video surveillance system throughout the data center facility, including critical areas such as entrances, server rooms, and equipment racks. Then, high-resolution cameras with both live monitoring and recording capabilities should be used. Consider implementing video analytics for advanced functionalities such as facial recognition or object tracking.
Zero Trust Physical Security
Regarding your physical security strategy, it’s important to consider zero trust. Although zero trust is often considered a cybersecurity strategy, it also applies to your physical security. You can’t trust every visitor, contractor, and interviewee entering your premises. So why should they be able to access your data centers and all rooms housing sensitive assets?
With a zero-trust Physical Security Infrastructure strategy, these rooms are secured with smart door locks. Users only gain access permissions to enter the spaces necessary for daily operations and nothing further. Securing these spaces allows you to enforce more stringent security for your valuable assets.
– Room security. This is the third line of defense, which aims to restrict intruders from accessing specific rooms or areas within the data center building or facility. Room security may include locks, doors, walls, cages, racks, cabinets, cameras, sensors, alarms, and guards.
– Device security. This is the fourth line of defense, which aims to protect individual devices or components within the data center rooms or areas. Device security may include locks, covers, seals, tamper-evident labels, encryption keys, passwords, and authentication mechanisms.
Perimeter Security
You can establish a secure perimeter around the data center facility for Physical Security Infrastructure. This may include tall fencing, walls, or bollards to deter unauthorized access. Consider integrating intrusion detection systems, such as motion sensors or CCTV cameras, to monitor and record any suspicious activities around the perimeter.
Also, you can implement robust access control measures to restrict entry to authorized personnel only. This can include a combination of physical barriers like turnstiles, mantraps, or security gates, as well as electronic systems such as biometric readers, smart cards, or keypads. Two-factor authentication is highly recommended for enhanced security.
Summary on Physical Security Infrastructure
Datacenter breaches lead to GDPR compliance infringement and potential legal issues for your business – which could be costly. By prioritizing physical and digital security, you can ensure that only authorized staff members, and high-level employees can access your most sensitive and critical resources.

Adhar Dhaval is experienced portfolio, program and project leader with demonstrated leadership in all phases of sales and service delivery of diverse technology solutions. He is a speaker sharing advice and industry perspective on emerging best practices in project leadership, program management, leadership and strategy. He is working for the Chair Leadership Co.