Data Access Control Through Online Identities

Table of Contents
Have you ever signed in to a website without having registered an account by using only your Google ID? This is a good example of an online identity. This same principle can be used by corporate organizations to allow employees to access a suite of resources on internal SaaS ecosystems. To allow the governance of these online identities, we believe that enterprises should strictly enforce comprehensive data access restrictions and checks throughout their SaaS application ecosystems. Vendors such as docontrol.io, for example, can track the use of resources and artifacts in SaaS systems with Single Sign On – SSO technology. This also includes permissions for hosted artifacts within SaaS services expiring automatically to prevent overexposure and reduce the overall attack surface.
What Are Online Identities?
Online identities, also called online personas, are user credentials that have a singular purpose which is to authenticate and verify a user’s identity and right to access online resources. The concept is based on active directory user accounts. This online identity is typically utilized to access SaaS applications like online email or internet banking etc.
Defining SSO
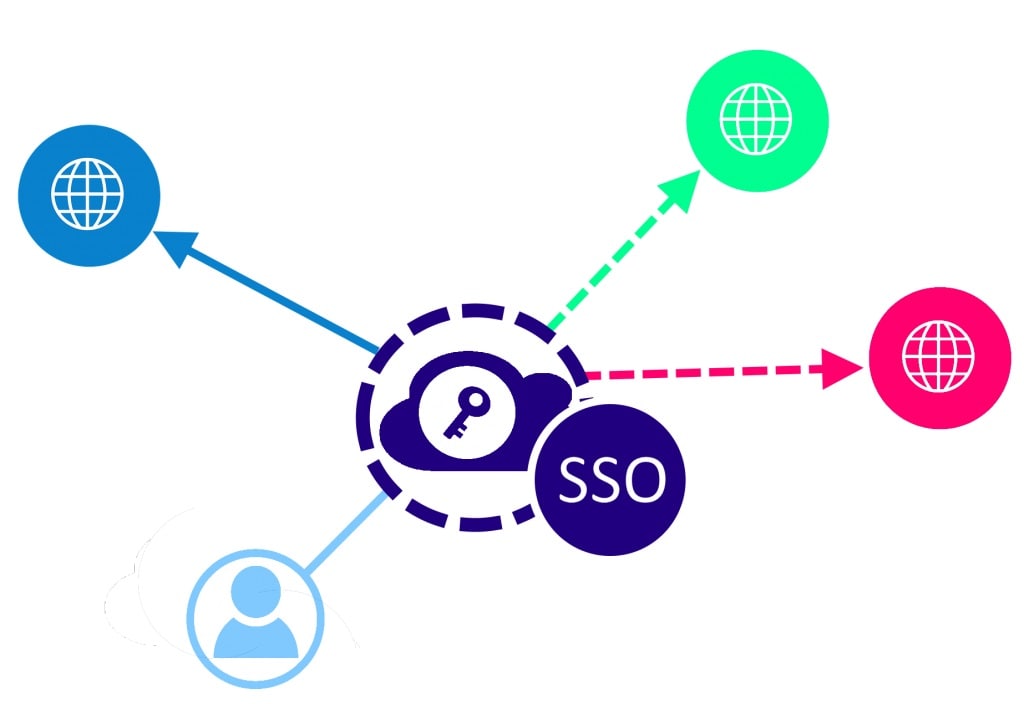
In a corporate environment, a similar use case for online identities exists called Single Sign-On (SSO). SSO authenticates users and allow them to gain access to corporate resources that are in the cloud. In an environment where a Microsoft tenant exists, for example, corporate resources are inside Microsoft’s Azure cloud. This is allowing employees to access SaaS applications like Office 365, SharePoint Document repository, and tools such as Microsoft Power BI. Such an online identity is typically based on a user account inside the organization’s active directory hive.
In order to make the most of Microsoft’s Azure cloud and its SSO capabilities, many organizations turn to Microsoft Azure consulting services. Azure consulting can provide expert guidance and support to help businesses implement and manage their Azure environment in a way that maximizes security, efficiency, and ease of use. With the right consulting partner, businesses can customize their SSO solutions to fit their specific needs and ensure seamless integration with their existing infrastructure.
Token Passing
This amazing feat is achieved using a concept called token passing. When an employee utilizes the SSO login the environment generates an impermanent token that represents the successful authentication of the user. This electronic token is then utilized as a proof of authentication allowing the user to access all attributed SaaS services in the organizational environment.
Furthermore, the SSO token is utilized both by browsers and applications.
Benefits of Corporate SSO
Some of the benefits of utilizing SSO in a corporate environment are the following:
- When new users are added to the organizational tenant, they can be added using a single user template, and gain immediate access to all their required SaaS resources.
- Users do not suffer from password fatigue.
- In line with the previous point is the benefit that users will inevitably experience better speed when online identities are seamlessly sync in the background to provide access to applications.
- Data access control can be in operation at a granular level by providing access to the employee. This would utilize the Zero Trust model, and access would need to be provisioned manually or through inheritance in objects like groups or folder.
Inceases IT and Employee Productivity
A single point of access will cut down on wastage of time and resources.
Lessen the number of support calls. Users who just need one password to access all of their applications won’t need it as often.
Enhancing the user experience. Users save between 5 and 15 seconds every login since there is no need to switch between numerous login URLs or change passwords.
Reduce security risks. Employees are not putting their security at risk by using their SSO login credentials on any device or web browser.
As you can see, one of the biggest advantages of single sign-on is its capacity to boost end users’ productivity.
Uses Risk-Based Authentication (RBA)
Here’s how adding Single Sign-on and RBA adds an additional degree of protection to online identities.
SSO allows your client or end-user a single “key” that they may use to sign in to many online domains, mobile applications, and third-party systems with.
You may combine SSO with risk-based authentication for even greater security (RBA). You and your security team can keep an eye on user behavior using RBA. In this method, you may request further identity verification if you see any strange user activity. This is including the usage of an incorrect IP address or repeated login failures. You may deny access to the user if they are unable to do this.
Organizational Risk Involved in SSO
Although this technology has many benefits it does introduce notable risk factors into a corporate SaaS environment.
- When a threat actor gains access to a user’s SSO credentials, such an attacker would have complete access to all the services and applications attributed to the user.
- If user access is incorrectly configured, users might gain access to resources they are not privileged to.
- Users then also can download such confidential information. And then transfer the data to an external device that is outside the organization’s control.
Addressing Organizational SSO Risks with Online Identities
The first line of defense in cyber security is the user’s password. Users need to use strong to complex passwords for their SSO accounts. Secondly, users need to understand the risk of using their corporate credentials for platforms such as webmail and social media.
To address the issue of erroneous access and consequential data leakage organizations can implement monitoring software in their SaaS environments. These monitoring solutions would then be able to report user access as well as the modification, removal, and migration of sensitive documents.
In Conclusion: How to Manage Online Identities
When it comes to corporate SaaS environments and the application of SSO to access resources, organizations need to implement policies that reflect the way SSO needs to be fully operational. This is especially true for inheritance and the ability to assign resources in the first place.

Ananya Prisha is an enterprise level Agile coach working out of Hyderabad (India) and also founder of High Level PM Consultancy. Her goal has been to keep on learning and at the same time give back to the community that has given her so much.