4 Most Common Malware Attacks To Watch Out For In 2023
Cybersecurity experts believe that security attacks will still be prevalent in 2023. Malicious attackers keep on evolving in their ways in order to continue taking advantage of security loopholes via malware attack threat. And it’s expected that some of the most common malware attacks will be more sophisticated than ever.
Table of Contents
Henceforth, it’s crucial for individuals and organizations to be aware of the different types of malware attackers will use in 2023. Understanding these threats can help prevent data loss and other damaging consequences of malware attacks.
Here are the most common malware attacks you need to watch out for:
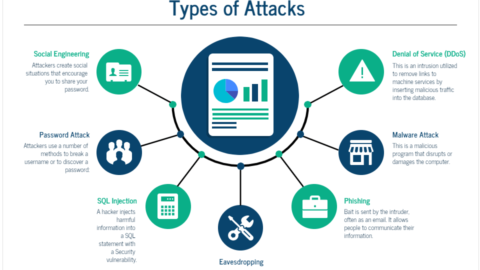
1. Computer Worm
A computer worm is one of the most common malware attacks to watch out for in 2023. According to the definition worm virus is a type of malware that replicates itself. It spreads to other devices on a network without any user interaction.
Once a worm infects a device, it can use that device to scan for and infect other vulnerable devices. It creates a chain reaction that can spread throughout an entire network.
There are several types of computer worms among common malware attacks, including:
- Email Worms: These worms spread through email attachments and can infect a victim’s computer when they open the attachment. The worm then shares the victim’s email contacts to other devices.
- Network Worms: These worms disperse through network connections as common malware attacks example. They can infect entire networks of computers. Network worms often exploit security vulnerabilities in operating systems and software to spread too.
- Instant Messaging: These worms distribute through instant messaging applications. They can infect a victim’s computer when they click a link or download a file sent through the messaging app.
- File-sharing Worms: File-sharing worms circulate through peer-to-peer file-sharing networks. They can infect a victim’s computer when they download an infected file.
Computer worms can affect individuals and organizations and inflict data loss, system crashes, and network downtime. Being vigilant and proactive reduces the risk of a devastating worm attack.
2. Ransomware
Ransomware attacks among common malware attacks involve encrypting a victim’s files. Then, the attacker will demand payment for the decryption key. The malware spreads through email attachments or links, and once it infects a system, the ransomware encrypts the files on that computer.
Here are some common types of ransomwares to watch out for in 2023:
- Crypto Ransomware: This ransomware encrypts files on a victim’s computer and demands payment for the decryption key.
- Locker Ransomware: Locker ransomware locks victims out of their computers, making it impossible to access any files or data. It then demands payment in exchange for unlocking the computer.
- Mobile Ransomware: Mobile ransomware attacks are becoming more common as more people use smartphones and tablets for work and personal use. These attacks involve locking a victim’s mobile device. Then, the attackers demand payment to unlock it.
If you become a ransomware attack victim, it’s best to report the incident to law enforcement agencies and not pay the ransom. Instead, work with a reputable cybersecurity firm to attempt to restore your files and prevent future attacks.
3. Keyloggers
Keyloggers are common malware attacks that records every keystroke on a victim’s computer or mobile device. Keystroke information keyloggers can get access to include usernames, passwords, and other sensitive information. Cybercriminals often use keyloggers to steal personal data, which will likely continue to be a threat in 2023.
The following are some common types of keyloggers in 2023:
- Software Keyloggers: These programs apply to a victim’s computer or mobile device. They’re often disguised as legitimate software. Once installed, software keyloggers record every keystroke made on the device.
- Hardware Keyloggers: These are physical devices attached to a victim’s computer. Hardware keyloggers capture every keystroke made on the keyboard, and they can be difficult to detect.
- Remote Access Keyloggers: These programs nestle on a victim’s computer or mobile device. Remote access keyloggers allow a cybercriminal to access the device and view every keystroke remotely.
Use strong passwords and two-factor authentication. The two can make it more difficult for cybercriminals to access your accounts even if they have captured your keystrokes.
4. Rootkits
Rootkits are malware that hides their presence on a victim’s computer or mobile device. Cybercriminals often use them to gain unauthorized access to a system, steal data, and carry out other malicious activities. Rootkits modify the operating system or other key system components to conceal their presence.
Some common malware attacks types of rootkits include:
- Kernel-Mode Rootkits: These operate at the operating system’s kernel level. Kernel-mode rootkits often use advanced techniques to hide their presence – usually involving hooking into system calls and intercepting network traffic.
- Bootloader Rootkits: These rootkits infect a victim’s computer’s bootloader. Cybercriminals often use bootloader rootkits to gain persistent access to a system, even if the operating system is reinstalled.
- Memory rootkits: These rootkits operate in a victim’s computer’s memory. It makes memory rootkits difficult to detect using traditional anti-malware tools. They often use direct kernel object manipulation (DKOM) and direct memory access (DMA) to hide their presence.
Be cautious when downloading and installing software as rootkits can sometimes bundle with legitimate software.
Takeaway on Common Malware Attacks
The threat of malware attacks will remain a significant concern for individuals and organizations in 2023. As cybercriminals continue to develop more sophisticated techniques, it’s crucial to stay vigilant and take steps to protect against these threats. Awareness and education are the best defenses against cyberattacks.

Valencina has more than 25 years of experience as an IT consultant with a great focus on enterprise application UI/UX. She has experience working across multiple industries, acting both in an advisory role, as well as hands on in the technical build of solutions. Valencina is the co-founder and COO of Nitera Training Services.