OT Security: Best Ways To Prevent OT Security System Vulnerabilities
Cyber attacks and hackers are every business owner’s biggest nightmare. Both IT and OT system environments have been victims of cyberattacks, and the threats are only getting more serious every day. A survey conducted by a cybersecurity firm Fortinet says that almost 90% of the firms using OT have experienced some sort of cyber attacks in the past year. Hackers are weaponizing OT attacks to the point that they can physically injure a human in the not-so-distant future. Therefore, if you are a business owner, you need to understand the importance of OT security. Investing in OT security can help prevent commercial vandalism and financial loss.
Table of Contents
What is OT security, and why should you be concerned about it?
OT systems have been put in place to regulate, automate and efficiently manage industrial machinery. Previously this was manually operated and handled by humans and was detached from IT environments. But this does not apply to our current situation.
The idea to converge physical machineries with IT systems was formed. This was possible due to sophisticated advances such as IoT sensors and actuators that could be fitted into physical equipment. This was a necessary innovation since it allowed wireless communication between a physical machine and an IT environment. The central system stores information and helps in the easy analysis of complex data generated through the machines. Further, this data can be used remotely through cloud services.
IT-OT convergence has taken place to introduce big data and smart analytics to the process. Taking such measures, in turn, enhances the capabilities of OT systems and also increases the efficiency.
However, with increased automation comes increased risk. The air gap between the IT and the OT systems is rapidly dwindling. Hence it is essential to know how best to protect your systems from malware and predatory hackers.
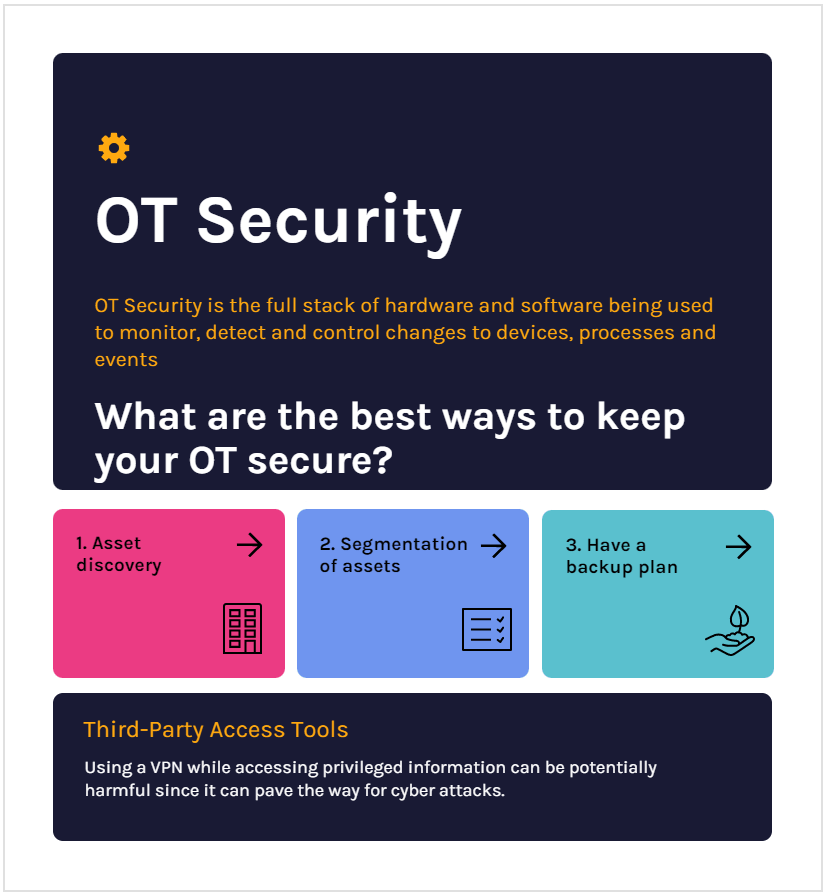
This is where an OT security vendor can come in handy. OT Security is the bundle of hardware and software being used to identify, monitor and control changes to devices, processes and events.
You can concentrate on making the most of your IT-OT convergence by cutting down on cost. While an OT security vendor can keep your OT systems secure by keeping a log of events and monitoring for vulnerabilities.
What are the best ways to keep your OT secure?
OT systems are usually put in place to last for decades hence being highly prone to malware and cyber-attacks. Malware can easily enter OT systems through IT environments and affect machinery. The risk is higher since OT systems cannot be frequently taken down for updates.
Thus it is vital to know a few best practices that you can implement to protect your systems better.
1. Asset discovery
OT networks are complex and require expertise in order to pinpoint vulnerabilities.
It is essential to assess and monitor Level 0 (Process level) and Level 1 (Basic control) devices as well. This includes a wide variety of instruments such as field devices, sensors, Distributed Control Systems (DCS), Programmable Logic Controllers (PLC), Safety Instrumented Systems (SIS.) However, these assets are often neglected.
Only the level 2 assets such as engineering stations, servers, routers, switches, etc., are often monitored and assessed. These come under Area supervisory control.
It is not easy to monitor because assets are distributed over a wide geographical area. And these systems are embedded with complex software and protocols. Thus it is very challenging to track vulnerabilities in these assets.
Having automated asset management and inventory can help assess vulnerabilities. Not to mention they ensure the continuation of the process reliably and safely.
2. Segmentation of assets
The rapidly dwindling air gap between the OT and the IT systems is an ever growing concern that needs to be taken care of.
In addition, segmentation is essential to protect legacy systems that were programmed to be connected to the Internet. This air gap segmentation can protect OT from breaches through that channel.
This can be replaced by setting up VLAN without spending too much money on it. VLAN helps restrict user access to specific segments of the network, thus giving access to only authorized personnel.
Network and asset segmentation can help protect the rest of the areas when a single site is breached.
In addition, a firewall with knowledge about the OT-specific protocols can be mounted. Mounting such a firewall can help screen for malicious content that might breach OT network segment boundaries.
Understand and develop a cyber risk assessment report for every OT asset.
Make sure to create an OT network map and assess OT and IT interdependencies.
3. Have a backup plan
In case of a breach in a particular system, it is essential to have workaround circuits. In addition the infected ICS system can be isolated. This prevents the infection from spreading to other regions thus compromising the entire system.
Develop a contingency plan and program it into your systems in case of malfunctioning or malware infection in a specific region.
Make sure to test these backup procedures from time to time. In addition, keep these backup plans away from any network connections. Ransomware attacks are common in the presence of an unencrypted network. Thus jeopardizing your safety net in case things go wrong.
Keep in place manual controls. Thus in case you need to take OT systems offline, you can still keep the process going through manual controls.
Always make sure to test these manual controls from time to time and update them if necessary.
OT Security & Third-Party Access Tools
Ever since the emergence of the Covid 19 pandemic, most of the workers have started working remotely. This made VPN usage reach an all-time high.
It can be a good idea to use VPN in case of giving access to non-sensitive parts such as emails. However, caution should be taken when providing access to privileged data and machinery.
Using a VPN while accessing privileged information can be potentially harmful since it can pave the way for cyber attacks. VPNs cannot enforce monitoring of sessions which is vital for security and overseeing privileged user access. Furthermore, it lacks the scalability, visibility, and cost-effectiveness. These factors are expected out of remote worker access.
Final thoughts
Establishing a cyber security protocol for OT is not as complex as setting up for IT. This is because an OT system does not attract as much traffic as an IT system. This makes assets easy to be monitored and inventoried.
Inventories can be easily used to detect unauthorized changes thus weeding out anomalies in earlier stages.
Providing the proper training to personnel and well-designed cyber security software is a must. It can help prevent cyber security threats to your systems.
Damage to OT platforms can have more staggering, long-lasting effects on a company financially. Therefore having a system in place can help prevent all these headaches.
Tell us any other measures you take to prevent security vulnerabilities in the comments below.
Dan has hands-on experience in writing on cybersecurity and digital marketing since 2007. He has been building teams and coaching others to foster innovation and solve real-time problems. Dan also enjoys photography and traveling.