How To Optimize Cloud Storage Without Compromising Security ?
Cloud storage optimization is an excellent option for businesses and individuals looking to store their files. It offers greater flexibility in where your files are located and how they’re shared with other users. You can access your files from any device with an internet connection, including smartphones and tablets. This makes it easier for employees to use assets on the go without having to carry their laptops around with them. However, it can be hard to find an exemplary cloud service without compromising your data security. If your provider doesn’t prioritize that, you’ll become vulnerable to threats like ransomware. As a result, your operations may suffer, straining your connections and costing you your customers. So, how to optimize Optimize Cloud Storage?
Table of Contents
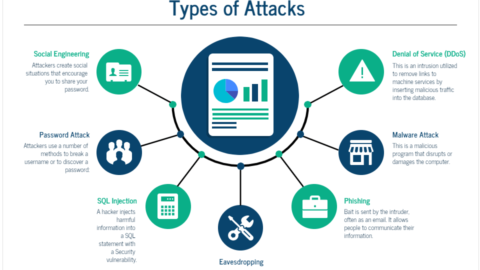
If you want to optimize your cloud storage without compromising safety, here are five tips and tricks you should follow:
-
Use Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring another factor besides your password. For example, you might type in a passcode sent via text message or use a unique app that generates a code every five minutes. This makes it harder for hackers and cybercriminals to breach a user’s account since they would need both the password and the secondary identification.
You can work with a high-quality IT support company in your area to implement two-factor authentication. It may provide you with a program that generates codes on your phone rather than a text message. While this may seem inconvenient at first, it’s much safer than short message service (SMS) verification because of how easily text messages can be intercepted by hackers monitoring your communications.
-
Encrypt Your Data to Optimize Cloud Storage
Encryption is the process of converting data into code, making it unreadable to anyone who doesn’t have the key to decipher it. With this, anybody who gains unauthorized access to your files can’t use them without first decrypting them. This robs them of an opportunity to sabotage your operations.
There are plenty of different encryption algorithms; some are more secure than others, and the ease of implementation also varies.
The most common option is advanced encryption standard (AES), which uses 128-bit or 256-bit keys. This kind of data encryption has compatibility across platforms and applications, which helps you keep your data safe even if the cloud service provider suffers a breach.
Another option is to use public key infrastructure (PKI) encryption, which allows users to share files without decrypting them first. PKI uses asymmetric cryptography. This means that you’ll need two keys: one private and one public. The private key must be kept secret; otherwise, anyone who gets hold of it will be able to decrypt your data.
-
Implement A Password Manager
Encrypting files and folders is only half the battle even it is done to optimize cloud storage. You also need to consider how you’re going to access them. If someone gets their hands on your password, they’ll be able to access all of your files, no matter how tight your security may be.
That’s why a password manager is essential, especially if you have multiple devices for work and personal tasks. A password manager stores all your passwords in an encrypted database so that only you can access them. This allows you to safely store passwords without compromising any of them in case someone gets their hands on your device or computer.

-
Incorporate Anonymization Services
Anonymization services have been around for a while now. You can use them to hide personal information stored in public databases. This means that if someone were to steal your details from a cloud storage service, they wouldn’t be able to connect those details with your real-world identity. These services work by replacing real names with pseudonyms, which makes it much harder for anyone to link them. How to optimize cloud storage with these services?
When using anonymization services to protect your cloud storage data, make sure you work with an accredited company that can guarantee the safety of your information. You should also check whether or not they offer encryption and pseudonymization. If you want your data to remain safe even if it gets stolen or leaked by accident, these are essential.
-
Ensure Proper Permissions Management
When you set up your cloud storage, ensure that only those who must use the data have access to it. This should be further limited to when they need it to do their jobs for cloud storage optimization.
This will help prevent unauthorized people from accessing sensitive information. It also ensures that no one person has too much power over another employee’s data.
For example, don’t give everyone on your team the ability to read or edit data. Instead, give them only those permissions that are necessary for their jobs. This will help prevent unauthorized access or data leaks caused by accidental file sharing.
Key Takeaway on Cloud Storage Optimization
To optimize Cloud storage, it is beneficial in storing your business data, but you must prioritize the safety of your data. Consider these five tips to make full use of this innovation without sacrificing security. Once you do so, you can sustain your company’s progress in the long run.
Make sure you are familiar with your cloud storage strategy’s architecture and that you are aware of where each type of data in order to mitigate dangers like these. In order to mark data and make it simpler to discover, you can also utilize the tagging tools that are present in the majority of cloud storage systems. For instance, if you must retain certain data for a predetermined amount of time due to compliance requirements, you may tag that data with tags and then delete it once the required retention period has passed.

Adhar Dhaval is experienced portfolio, program and project leader with demonstrated leadership in all phases of sales and service delivery of diverse technology solutions. He is a speaker sharing advice and industry perspective on emerging best practices in project leadership, program management, leadership and strategy. He is working for the Chair Leadership Co.