From Zero to Hero: Mastering Software Development in the Cyber Age
In the cyber age, where digital technology has permeated every aspect of our lives, mastering software development has become more crucial than ever. Software is vital in powering applications, systems, and services that drive our modern society.
Table of Contents
However, this era also brings forth new challenges, primarily related to cybersecurity. With the ever-increasing frequency and sophistication of cyber threats, software development companies must equip themselves with the knowledge and skills to develop secure and resilient applications.
Moreover, mastering software development in the cyber age requires a multifaceted approach. It entails a strong foundation in programming and a deep understanding of cybersecurity principles and practices.
Mastering Software Development

Mastering software development in the cyber age requires a combination of technical skills, adaptability, and a deep understanding of cybersecurity principles.
In this rapidly evolving digital landscape, where threats are constantly emerging, every software developer company must stay ahead of the curve and ensure the security and integrity of their applications.
Here are some key areas to focus on when mastering software development in the cyber age:
Strong Foundation in Programming
Begin by building a strong foundation in programming languages such as Python, Java, C++, or JavaScript.
Understanding data structures, algorithms, and software design principles will provide any software development company with a solid base for developing secure and robust applications.
Secure Coding Practices
Emphasize secure coding practices from the start. Follow established guidelines, such as the Open Web Application Security Project (OWASP) Top Ten, to mitigate common vulnerabilities, such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF).
Cybersecurity Awareness
Develop a comprehensive understanding of cybersecurity concepts, including threat modeling, risk assessment, encryption, authentication, and access control.
We suggest every software development company stay updated with the latest security vulnerabilities and techniques to defend against them.
Secure Software Development Lifecycle (SDLC)
Incorporate security throughout the software development lifecycle. Implement secure coding practices, conduct thorough security testing, and perform code reviews to identify and remediate vulnerabilities early in development.
Web Application Security
Understand the specific security challenges associated with web application development. Familiarize yourself with concepts such as secure session management, input validation, secure file handling, and secure communication protocols (e.g., HTTPS).
Secure APIs and Microservices
As software systems become more distributed and interconnected, secure design and implementation of APIs and microservices are crucial.
When designing and developing APIs, software development companies must learn about authentication, authorization, input validation, and secure data transmission.
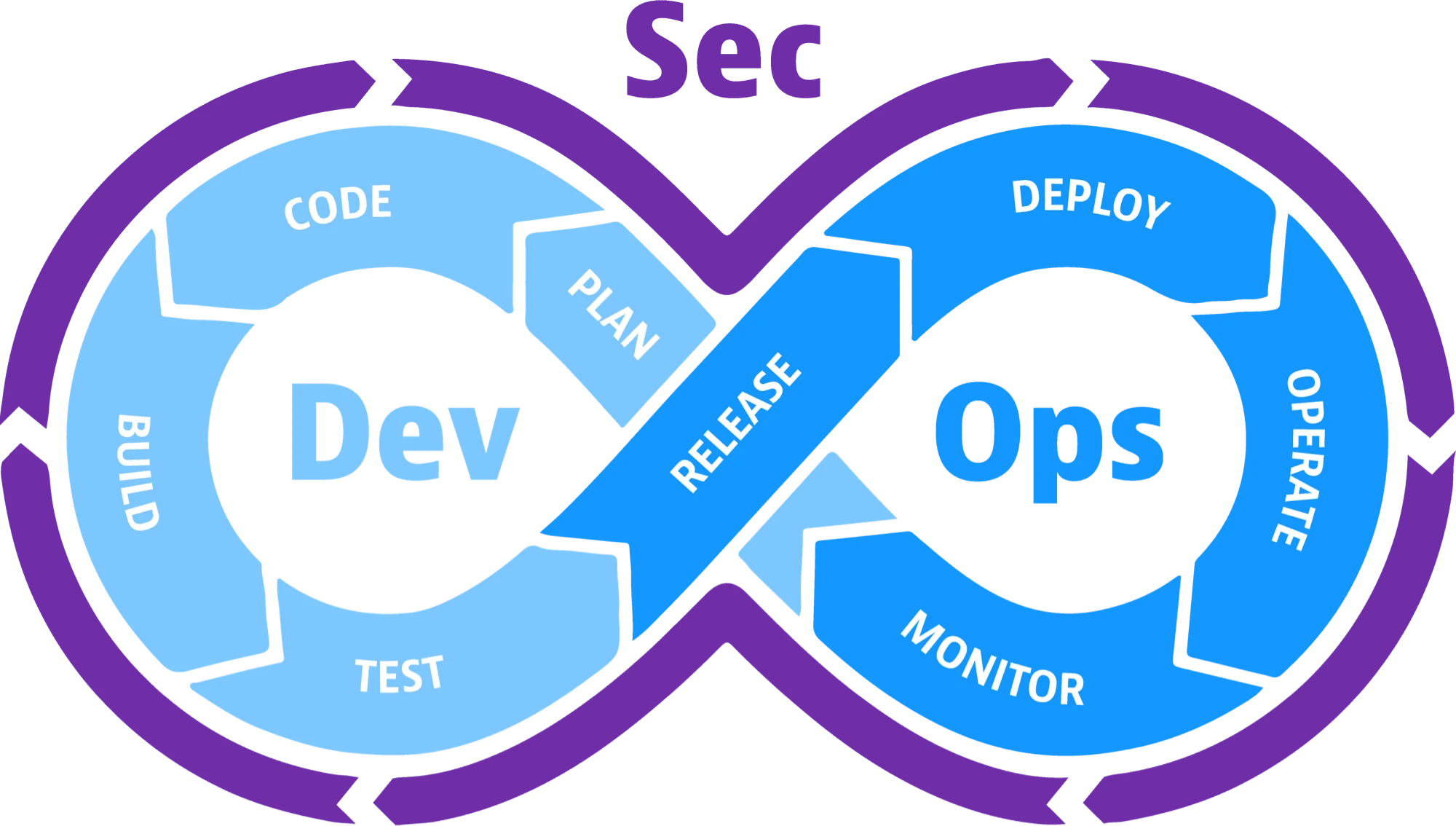
DevSecOps
Embrace a DevSecOps culture by integrating security practices into the development and deployment pipeline.
Use automated security testing tools, implement continuous integration and deployment (CI/CD), and promote collaboration between development, operations, and security teams.
Cloud Security
With the widespread adoption of cloud computing, understanding cloud security principles and best practices is vital. Learn about secure cloud architecture, identity and access management (IAM), encryption, and monitoring in cloud environments.
Threat Modeling and Risk Assessment
Develop the ability to identify potential threats and assess their impact. Perform threat modeling exercises to analyze and mitigate risks in software systems. Consider factors such as data breaches, privacy concerns, and regulatory compliance.
Continuous Learning
Stay curious and committed to continuous learning. Follow industry trends, attend conferences, participate in online communities, and engage in cybersecurity-related blog and forums.
Seek certifications like Certified Secure Software Lifecycle Professional (CSSLP) or Certified Ethical Hacker (CEH) to enhance your knowledge and credibility.
Factors To Consider When Mastering Software Development In The Cyber Age
Here are a few additional factors to consider when mastering software development in the cyber age:
-
Secure Authentication and Authorization
Implement secure authentication mechanisms, such as multi-factor authentication (MFA), to verify the identities of users accessing your applications. Employ strong authorization controls to ensure users have appropriate access levels and permissions.
-
Data Protection and Privacy
Understand data protection laws and regulations that apply to your software, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). Implement measures like data encryption, secure data storage, and anonymization techniques to protect sensitive user information.
-
Secure Code Review and Testing
Perform regular code reviews and security testing to identify vulnerabilities and weaknesses in your software. Use static code analysis tools, dynamic application security testing (DAST), and penetration testing to uncover potential security flaws.
Wrapping Up
By incorporating secure coding practices, adopting a security-first mindset, and integrating cybersecurity throughout the software development lifecycle, any software development company can build applications that protect user data, preserve privacy, and maintain the trust of their users.
As you embark on your journey to master software development in the cyber age, embrace the principles of secure coding, prioritize user privacy and data protection, and cultivate a proactive and security-conscious mindset. By doing so, you will be equipped to build software that meets the demands of the cyber age and contributes to a safer and more secure digital ecosystem.

Magdalena Polka is a Business Solution Designer and an Information Technology / Project Management consultant and author with over 15 years of software development, management and project management experience.